Pi and I
Setting up my Raspberry Pi. Experiences with crunchbang, ubunutu, bunsenlabs help, but in Raspbian some things still are slightly different, namely:
(1) Autostart
Autostart file is at /etc/xdg/lxsession/LXDE-pi/auto. Add programmes preceded by “@”
A Reader!
Academic publishing can sometimes be pretty much of a one way radio: You’re broadcasting but you never know whether or not someone is receiving – and if someone is receiving, what they make of it.
So I am happy that Dr Dominik Zink of the University of Trier took the time to read and kindly review my PhD Thesis in The Year’s Work in Modern Language Studies 79 (2019) 1, p 555 (published online on 28 March 2019 at https://brill.com/view/journals/ywml/79/1/article-p555_41.xml).
NextGen vanishes on front page
My NextGen gallery kept vanishing on my WordPress frontpage. It did not show as long as the page was set to front page, as soon as I picked a different front page, the images reappeared. Even when I changed the theme, the gallery disappeared.
I checked and rechecked the source code, but what I apparently missed was the gallery being wrapped in auto excerpt tags:
How to Stream Music from Linux PC to iPhone over Wifi
Option 1: UPnP
Universal Plug and Play (UpnP) is developed by the Digital Living Network Alliance (DLNA) and has interoperateability in mind. See Make Use Of for a list of possibilities.
- Server: Subsonic
- Install from here http://www.subsonic.org/pages/installation.jsp
Costs $1/month to use pro features - Get started here http://www.subsonic.org/pages/getting-started.jsp
Client: pick one from http://www.subsonic.org/pages/apps.jsp. VLC also works as a client, see https://askubuntu.com/a/109083/80611
I use play:Sub, another $5
I also tried Gerbera- Add Gerbera-ppa. If you ar not using ubuntu (but, say, Debian or Bunsenlabs) see astarix for help.
- Install Gerbera. apt-get said “Unable to correct problems, you have held broken packages. Used aptitude instead (see here)
- Failed.
Option 2: DAAP
Easy, cheap, but flawed.
- Server: Install Rhythmbox → open plugins → enable “DAAP Music Sharing” (obviously install if it is not there) → right click → properties → enter name and tick “Share my music”. Done.
- Client: Install “Simple DAAP” from app store. Open, find your server, done. I keep getting error -1004 and even though the phone can see the server it does not connect. Since DAAP is a proprietary protocol invented by…Apple, you would expect that there are options. But as there’s no native app that can do it and Simple DAAP is the only lonely player in the field, there aren’t. Except of course you find a broken android phone, install Music Pump (costs) or DAAP media player (free) and in under the minute you’re dancing around the house streaming.
Hat tip: Lifewire
Video
Interestingly it was easier to setup video streaming than audio (use vlcstreamer, see upubuntu).
- Install from here http://www.subsonic.org/pages/installation.jsp
It finally happened

I started by going to the library one or two nights a week and, once a window of opportunity presented itself, went part time. When I saw that »corruption in German literature« should work well, in 2011/2012 I took a sabbatical in order to write a proposal that would get me funded.
After several applications and interviews in Vienna, Walferdange, Berlin and Munich I settled on Munich. So in June 2012 I began writing properly while commuting from Vienna to Munich every other week. My »office« was in the Arbeiterkammer library and the Ludwig-Wittgenstein-Lesesaal in the Austrian National library.
In October 2015 I was ready and submitted the thesis.
You should think there is a sensation of great relief when you finally hand the work of three plus years over to the officer, but somehow there wasn’t. My defense was going to be in February 2016, so I started preparing the three talks I had to give straight away.
Now, with the defense out of the way, there still was no sense of accomplishment, because you have to publish in order to close the process. So off we go to finding a publisher, setting up the text according to the publisher’s style guides, resetting tables and trees because they don’t fit on the smaller pages any more, brainstorming a cover image with Marianne Vlaschits, test printing and changing the cover three dozen times because the digital printer does not approve of the background color. Then seeing the table of contents in a friend’s brand new book and going back to my own because I absolutely wanted one like it. And on and on.
In the end, thanks to the knowledge, understanding and patience of the good people at UniPrint Siegen, there is a finished product that does make me happy – but still fails to deliver the wash of relief. Because now five books have to get to Munich university library, where the people are not happy. My books lack the title page the faculty requires. When that is adressed, I get told to contact the officer who received the first version in 2015 again in four to eight weeks for the certificate. Which I recieved two weeks ago. The End.

Here it is:
Jan Söhlke: »verderben, verführen, verwüsten, bestechen«. Literatur und Korruption um 1800. Siegen 2017, 284 pages.
ISBN: 978-3-936533-81-1
For EUR 12.80 you can order the book at universi (Siegen University Press), you can download it from OPUS (Siegen university’s open access) for free or get it from the source while you’re here.
The back cover reads
Der von Max Weber für die Zeit um 1800 diagnostizierte Übergang von einem patrimonialen zu einem bürokratischen Herrschaftssystem ist mit Roger Callois zugleich faßbar als Wechsel vom aleatorischen zum agônalen Prinzip. Unter dem Vorzeichen der Korruption wird jener Übergang beschreibbar als Wandel von einem Paradigma der Kriecherei hin zu einem der Bestechung.
Diese bisher kaum eingenommene Perspektive ermöglicht es, die sich wechselseitig bedingenden und durchdringenden moralischen, politischen, juristischen und ökonomischen Implikationen der Modernisierung freizulegen. Eine umfassende begriffsgeschichtliche Analyse der semantischen, historischen und sozialen Verfasstheit von »Korruption« bildet die Grundlage für Lektüren von Lessings Minna von Barnhelm, Kleists Der zerbrochne Krug und Schillers Der Geisterseher. Drei kanonische Texte werden so in einer überraschenden Konstellation neu lesbar – und lassen ihrerseits unser Verständnis von Korruption in einem neuen Zwielicht erscheinen.
Mendeley Migration
sudo apt-get install sqlitebrowsercd ~/.local/share/data/Mendeley\ Ltd./Mendeley\ Desktop/sqlitebrowser <you@whatever>@www.mendeley.com.sqlite- Go to »Execute sql«-tab
-
update Files set localUrl = replace(localUrl, 'file:///old/path/‘, 'file:///media/new/path/‘);
- click »Execute« (or F5 or ctrl+return)
- click »Write changes«
- Done. Easy, right?
Thanks to 3.14a and jordi’s comment there. For related Mendeley grievances see khufkens, who can tell you how to sync Mendeley to your own server (instead of feeding Elsevier’s questionable pricing model).
Connect Crunchbang Linux to Bluetooth Speaker

I got myself one of these and after setting it up properly I must say that while I am a bit disappointed by the reach, I am very impressed with the sound quality for this kind of money (a white label apparently as »C26« sells under various brands and for different prices).
Anyway, the whole setup was a true Linux afternoon, reminding me of my NDISwrapper-days, just like it was 2006 again.
First, It took me a while to get crunchbang to discover the device and connect [1] (Blueman works much better as a bluetooth manager). Then apparently I manually needed to let pulseaudio know where to send the audio [2]. Atfer fiddling with some files, pulseaudio was broken, so I needed to reinstall [3]. Finally, the sound was much poorer than via my phone. I don’t know if I overlooked it or if loading rtirq changed something [4], but in the volume control center of pulseaudio there is a tab called »configuration« where I had to choose »High Fidelity Playback (A2DP)« to get decent sound (instead of »Telephony Duplex (HSP/HFP)« or »off«). Now most of the times it changes to the Bluetooth-device automatically once I switch it on and back when I switch it off. Sometimes not. But hey.
The sources I used were these:
- How to make pulseaudio bluetooth-ready: http://askubuntu.com/a/223203/80611
- How to switch the sink in pulse audio: http://askubuntu.com/a/108882/80611
- How to clean up after you screw up (which I did), i.e. reinstall pulseaudio: http://askubuntu.com/a/435221/80611
- How to improve the sound once it works but reminds you of a telephone: http://askubuntu.com/a/520384/80611 and https://wiki.ubuntu.com/UbuntuStudio/rtirq
German UNCAC Ratification is Lipstick on a Pig
Das im Februar beschlossene Gesetz gegen Abgeordnetenbestechung ist weitgehend wirkungslos. Ein Staatsanwalt muss nämlich nachweisen, dass ein korrupter Volksvertreter »im Auftrag oder auf Weisung« gehandelt hat. Wer sich nicht allzu dumm anstellt, hat strafrechtlich nichts zu befürchten.
The law against bribing of MPs is mostly useless as prosecution has to prove that a corrupt representative has been »either instructed or ordered« to act in a certain way. For the slightest chance of criminal liability under the new law, a parliamentarian would need to act in a pretty stupid way.
abgeordnetenwatch.de: Bundestag ratifiziert UNCAC – nach 11 Jahren (29. September 2014)
Some background can be found in my earlier post »Bribing MPs soon illegal in Germany«.
Automatically batch rename photo files
Preliminaries
What I get when I come home is file names looking like this: _DSC1234.NEF. What I wanted instead was
- date-shot in YYYYMMDD-format plus
- a descriptive shoot-name plus
- image-number
looking like this: 20140708_WeddingAdamAndEve_0001.NEF
There are a few issues with this:
ad 1. Date Shot: sometimes I can only copy and rename the files a few days after shooting, so the date should reflect the date the picture was taken, not the date it was copied. Getting date-shot from the file itself is difficult as there is no birth time recorded. The closest is mtime which is the time the file’s content has last been modified. However, creation date is stored in image file’s EXIF data.
ad 2: Name of Shoot: Ideally I wanted this to be a variable I could set as a parameter when calling the script.
ad 3. Number of Image: This should reflect the age of the image with the oldest one having the lowest number. The problem is that cameras usually restart numbering at 0000 once they hit 9999. So images n-9999 can potentially be older than 0000-n. I needed a solution that would cater for this special case.
The code
# original solution by @Gilles (http://unix.stackexchange.com/questions/141138/) # set base path and navigate to "basepath + parameter 1" BASEPATH='/media/data/photo/'; cd $BASEPATH$1 # add "EXIF creation time" as prefix to original file names exiv2 mv -r %Y%m%d-%H%M%S:basename: *.NEF # Now we have files with names like 20140630-235958_DSC1234.NEF. # final rename i=10000 for x in *.NEF; do i=$((i+1)) mv "$x" "${x%-*}_$2-${i#1}_Copyright-Jan-Soehlke.NEF" done
Walkthrough
Line 4: Here we set our base path. We choose the highest directory ever useed to store pictures.
Line 5: Navigate to base path + parameter 1. If our script is called rename and the pictures are in /media/data/photo/weddings/adam+eve, then we call the script through
./rename weddings/adam+eve
Line 8: In a first iteration we add EXIF-creation time as a prefix to the original file names. We use exiv2 for this operation. -r is for rename and we use YYYYMMDD-hhmmss, which is %Y%m%d-%H%M%S in strftime(3), plus :basename: to keep the original filename after the time stamp.
Through creation time as a prefix we now sort files by age, even if the files would sort differently by name. This could happen if during a shoot we reach 9999 and the camera’s counter continues at 0000 or if we shot with two different cameras.
By also retaining the original file name for now, we make sure that in case there are multiple files with the same time stamp, they still have individual names. EXIF time’s finest unit is a second, so if we fire bursts of images (Nikon’s D4s for example shoots at 11 frames/second), we have multiple files with the same creation date and thus potentially 11 files with the same name.
Line 12: The counter variable i counts from 10000 and is used with the leading 1 digit stripped; this is a trick to get the leading zeros so that all counter values have the same number. If you want more (or less) than four digits, set i accordingly.
Line 15: ${x%-*} removes everything that follows the - character, in our case it is hours, minutes and seconds as well as the original filename. ${i#1} writes the new four digit file number.
$2 provides a second variable, which we use for the shoot name. In this case we want it to be WeddingAdamAndEve, so we call the script through
./rename weddings/adam+eve WeddingAdamAndEve
Finally, I added _Copyright-Jan-Soehlke. It not only reminds someone who downloads the file that it is indeed copyrighted, it also helps with SEO as my name is automatically associated with each image I upload.
Possible Problems
a) The original file names already have a
-in place. In this case change the - in line 8 to something different (like _) and use the same character in the ${x%-*}-part in line 15 (in this case ${x%_*}, otherwise the script will not work as intended.b) A burst of images reaches across the
9999/0000-mark. These specific files will not be in order after renaming – but they weren’t in order in the first place, so I have no idea how to tackle this rare scenario other than by setting your camera’s counter to reset to 0000 after each formatting.c) Your files do not contain EXIF data. In this case see mikeserv’s solution which uses a different angle of attack and is thoroughly and well explained.
___________________________
* Stackexchange uses the CC-BY-SA license, so all the code in this example is naturally also CC-BY-SA.
Crunchbang on x200s
Rawtherapee
A slightly outdated version is in debian’s repositories, but if you want a newer one, go to »Kbyte’s Hideout«. Download .deb package and dpkg -i rawtherapee_<xxx>.deb
If there are unsolved dependencies: apt-get install -f and then dpkg -i rawtherapee_<xxx>.deb
Picasa
Well.
It still is the most straightforward programme I know for editing, simple retouches and exporting smaller sizes. I’m not happy with wine, I’m not happy with a google tool, but I cannot and cannot find an alternative (see here). Hence:
before following the webupd8 tutorial I needed
apt-get install libwine-cms:i386
After installation, use
cd ~/.wine/drive_c/Program\ Files/Google/Picasa3 && wine Picasa3.exe
to launch it.
If you would then create a script called »picasa« somewhere, say in ~/scripts containing the following:
#!/bin/bash cd ~/.wine/drive_c/Program\ Files/Google/Picasa3 &amp;amp;&amp;amp; wine Picasa3.exe exit 0
Picasa can then be launched from command-line with a simple »picasa« after a final
sudo ln -s ~/scripts/picasa /usr/bin/picasa
Clock
To change the format from Hour:Minute open ~/.config/tint2/tint2rc and consult strftime-man to change to your liking.
Change Key Bindings
Keyboard shortcuts can be changed in ~/.config/openbox/rc.xml
After saving, go to Openbox menu > Preferences > Openbox Config > Reconfigure. (Thanks, MysteryMember)
Redecorating the place II
Polypager’s strength clearly was in handling the database – it has foreign key capability and without the faintest complaint, Polly will display any mysql-database it is being fed. However, it was never built with serving images as a central part in mind. There is a gallery plugin in place, but my desires soon surpassed the capabilities.
Zenphoto in turn is fantastic in handling text and images (and video by the way, which surprisingly posed the biggest hurdle in wordpress – the other was 301, but in the end Tony McCreath’s redirect generator helped). The problem with zenphoto is more an aesthetic one as the available skins are limited and don’t really meet my expectations. The one I hacked together unfortunately »grew organically« over the years until recently it gracefully started falling apart.
Thus, today I make the move to WordPress and while I am at ease parting from Zenphoto, leaving Polly behind really hurts. So, thanks Nic for developing it and having me aboard, because in the process, I learned many a thing about distinguishing sensible feature requests from the other ones, about version management using svn and git, and also, in 2008, about how it feels to be at the receiving end of a proper hack.
Bribing MPs soon illegal in Germany
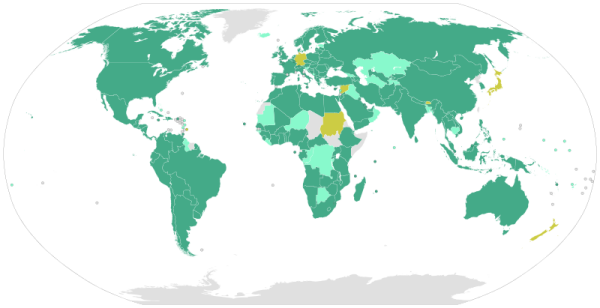
World map with United Nations Convention against Corruption ratifiers in green and signatories in orange (as of Feb 2014). Source: en.wikipedia.org – CC BY-SA 3.0
As the vote was paired with that one the considerable raise the MPs allowed themselves, I have the impression it somehow did not receive that much media coverage:
- Transparency International has some details and they also explain, why the law still has a very narrow definition of bribery (in English)
- Background reporting by Legal Tribune (in German)
- Article in Sueddeutsche Zeitung where it is mentioned towards the end (in German)
Human Nascars
MTPFS FAIL
sudo add-apt-repository ppa:webupd8team/unstable
sudo apt-get update
sudo apt-get install go-mtpfs
Optional:
sudo apt-get install go-mtpfs-unity
Mount:
go-mtpfs /media/MyAndroid
Unmount:
fusermount -u /media/MyAndroid
Ironic that I should now need a special programme to mount my one Linux device on my other Linux device while windows works out of the box…
Fabulous Fab and Obama’s Promise
An unrelated article over at Techdirt asks what happened to Obamas election campaign promise to protect whistlblowers. The interesting bit from Obama’s ethics agenda read
=&0=&: Often the best source of information about waste, fraud, and abuse in government is an existing government employee committed to public integrity and willing to speak out. Such acts of courage and patriotism, which can sometimes save lives and often save taxpayer dollars, should be encouraged rather than stifled. We need to empower federal employees as watchdogs of wrongdoing and partners in performance. Barack Obama will strengthen whistleblower laws to protect federal workers who expose waste, fraud, and abuse of authority in government. Obama will ensure that federal agencies expedite the process for reviewing whistleblower claims and whistleblowers have full access to courts and due process.
change.gov: Ethics Agenda
Funny, innit?
Prescription Drugs and Corruption
The highlights:
- There is evidence that about 90 percent of all new drugs approved by the FDA over the past 30 years are little or no more effective for patients than existing drugs.
- Every week, about 2.400 excess deaths occur in the United States among people taking properly prescribed drugs to be healthier.
- Prescription drugs are the 4th leading cause of death.
- There is systematic, quantitative evidence that, since the industry started making large contributions to the FDA for reviewing its drugs, the FDA has sped up the review process with the result that drugs approved are significantly more likely to cause serious harm, hospitalizations, and deaths.
Network Sync
Setting it up was a lot easier then I though. All it took was rbgeek’s exccellent article »File Synchronization Between Two Ubuntu Servers using Unison«.
Falko Timme’s article »Setting Up Unison File Synchronization Between Two Servers On Debian Squeeze« at howtoforge was also helpful. Another insightful article is Chris Lale’s »Synchronising laptop and desktop files using Unison« at Sourceforge.
One issue: normally your device gets an IP address automatically from your router. Unison settings depend on the IP address (for ssh connection), so if the IP address changes, Unison gets confused. Thus, we want a static IP address on the remote machine. Johnathan Hobson’s »Networking Tips and Tricks« are a good start. The settings that finally worked for me I got via chili555’s post on ubuntuforums. Using Netman’s GUI, I set:
Method: Manual
Address: 192.168.0.9
Netmask: 255.255.255.0
Gateway: 192.168.0.1
DNS Servers: 8.8.8.8, 192.168.0.1
Search domains: –
I understand little, but what I do understand is this:
- »address« needs to be outside the router’s scope. Mine is configured to start at 10, so I picked 9.
- »gateway« simply seems to be the router’s ip-address
- »DNS-Servers«: no clue why 8.8.8.8, the other again seems to be router’s ip address
You can easily determine the router’s ip-address and the scope for auto DHCP from the router’s admin interface.
Other useful information and resources
SSH
- SSH Guide [help.ubuntu]
- SSH-Question [ubuntu forums]
Unison
- Unison
- Unison Howto
- Unison Tutorial [softprayog.in]
- Unison case involving SSH [Linuxjournal]
Alternatives
- Owncloud (see here for my setup)
- Sync files on Ubuntu oneWhich I wouldn’t like for it absolutely insists that it has to dwell in /home
- Share a folder via samba
[article started in January 2013; final, rewritten version from January 2014]
Medical Practitioners cannot be Corrupt
The good news is that German health minister Daniel Bahr is about to change that.
Update Nov 2014: The bad news is, that the bill did not pass the Bundesrat. And coverage is pretty much non-existent since then.
Custom Shortcuts in Kile
It’s very easy and very fantastic: User defined Tags.
Mining Data

»Overview –
through Hollerith Punch Cards«
Motherboard has an insightful article on the history and future of Diaspora (an open source, distributed alternative to Facebook). The article is very long and alongside the Diaspora-narrative there are several other issues it focuses on. One of them deals with data mining, which – with Facebook as a regular dinner table subject – is touched upon frequently around here.
The argument I hear most often when it comes to privacy issues is »I can’t see how this bit of information could possibly be vital or interesting to a third party«. The thing with data mining is of course the three-letter-word above »argument« lacks: now.
Sooner or later someone might (or might not) come along who can see a relevance, even long after the information is in the open. And often it is not the data in itself that turns out to be explosive, but a new way in which it is connected to other harmless data. Or a new place it’s brought to.
Here’s one fun example from the Diaspora-article:
Last week, the Financial Times reported that a newly uncovered deal between Facebook and the data firm Datalogix allows the site to track whether ads seen on Facebook lead users to buy those products in stores, which is highly attractive intelligence for advertisers. (Datalogix does this by buying consumer loyalty data from retailers, and tracks in-store purchases by matching email addresses in its database to email accounts used to set up Facebook profiles, along with other account registration information.)
Alec Liu (2 Oct 2012): What Happened to the Facebook Killer? It’s Complicated. Motherboard.
The future implications of the email address mix-and-match is not fully clear yet (although for a start I think it’s of nobody’s business what I buy where). But there are other examples where the consequences are very clear. For instance someone disclosed his credit card number to both Apple and Amazon. Ultimately this led to the destruction of his digital life – email account takeover, twitter account takeover, phone wiped clean, computers wiped clean: proudly brought to you by small-scale data mining with a pinch of social engineering thrown in:
Amazon tech support gave them the ability to see a piece of information — a partial credit card number — that Apple used to release information. In short, the very four digits that Amazon considers unimportant enough to display in the clear on the web are precisely the same ones that Apple considers secure enough to perform identity verification.
Mat Honan (6 Aug 2012): How Apple and Amazon Security Flaws Led to My Epic Hacking. Wired.
And finally, my historian-friend’s favourite – and at the same time the most ghastly – data mining example of them all is how the 1933 census in Germany was later used to organise the deportation of Jews:
But Jews could not hide from millions of punch cards thudding through Hollerith machines, comparing names across generations, address changes across regions, family trees and personal data across unending registries. It did not matter that the required forms or questionnaires were filled in by leaking pens and barely sharpened pencils, only that they were later tabulated and sorted by IBM’s precision technology.
Edwin Black (2009): IBM and the Holocaust. Washington DC, p. 107.
Update 4 Aug 2013: I recently learned about the Rosa Liste (pink list). This list was kept by the German empire and subsequently the Republic of Weimar to monitor male homosexuals. In 1933 the list fell into the hands of the new government which used it to go straight from monitor to murder. Case in Point: you never know what the meaning of any given datum is going to be in the future.
Overheating Thinkpad T60
The problem is described in many places and many different fixes, remedies and work arounds exist. Most of them lack proper documentation, so I am reluctant to try them. Even thinkfan, which is quite popular, scares me more than it helps.
Here is a collection of relevant information I found:
- Bug report at launchpad
https://bugs.launchpad.net/ubuntu/+source/linux/+bug/751689 - Show temperatures of all sensors
cat /proc/acpi/ibm/thermal
- Show Speed of fan
cat /proc/acpi/ibm/fan
- Thermal Sensors
http://www.thinkwiki.org/wiki/Thermal_sensors - List of ways to control fan speeds at Thinkwiki.org
http://www.thinkwiki.org/wiki/How_to_control_fan_speed - Thread at askubuntu
http://askubuntu.com/questions/178467/thinkpad-fan-control-error - Howto at NeoLocus
http://blog.neolocus.com/2012/07/lenovo-thinkpad-x61-temperature-and-fan.html - Howto at thinkwiki.de [in German]:
http://thinkwiki.de/Thinkfan
For now I went with #7 (thinkfan howto by Neolocus), and I do hear a substantial difference in fan activity – but I am still scared.
Top 10 Corruption Sentences
- Joel Esquenazi
- Rod Blagojevich
- Viktor Bout
- James Ibori
- R. Allen Stanford
- Jimmy Dimora
- Matthew Ng
- Albert “Jack” Stanley and Jeffrey Tesler
- Jean Rene Duperval
- Gerhard Gribkowsky
More on the background on each of the cases in Samuel Rubenfeld’s article.
Bibtex going openout_any = p
bibtex <project-path>/src.aux
I got:
bibtex: Not writing to &amp;lt;project-path&amp;gt;/src.blg (openout_any = p).
I couldn't open file name `&amp;lt;project-path&amp;gt;/src.blg'
To get rid of the error, open texmf.cnf, which resides in /usr/share/texlive/texmf/web2c through
sudo gedit /usr/share/texlive/texmf/web2c/texmf.cnf
Then find the entry
openout_any = p
p is the paranoid setting. I changed it to r and it now works again (chapeau to dmj).
[update 31 Jan 2013] If sudo is not an option and thus texmf.cnf can’t be changed, see Sini’s helpful comment below. [/update]
If you want to learn about multiple bibliographies using multibib, there is a very good tutorial by peisistratos. Unfortunately it is in German, but I’m sure there are English ones out there, too.
Can We Buy Your Loyalty?
brought the most significant changes to financial regulation in the United States since the regulatory reform that followed the Great Depression.
Wikipedia: Dodd–Frank Wall Street Reform and Consumer Protection Act (ret. 5.9.2012).
The Dodd-Frank-Act also introduced a »whistleblower bounty programme« (under Title IX, subtitle B). It means whistleblowers can get paid for releasing information, and today FCPA-Blog reports that the first one just took home a prize of US $ 50.000.
It is startling that in a sense we are now trying to bribe people so they blow the whistle on corruption. The moral implications are interesting: not only will people get paid to abide by the law, but, after all, an employee (or agent) owes a certain amount of loyalty to the employer (or principal). There are corruption theories that define corruption exactly as not honouring that loyalty in order to achieve personal gain. But the economical implications are at least as intriguing: loyalty suddenly becomes a scarce commodity and it would not at all surprise me to see prices going up and going up fast. Apparently, a reward substantially helps people discover their loyalty to law (and their community):
since the SEC’s whistleblower program started in August 2011, the agency said it has received about eight tips a day. Using a conservative count, that means at least 1,600 whistleblower complaints have been filed.
Richard L. Cassin (5.9.2012): Six Lessons from the SEC’s First Whistleblower Reward. FCPA-Blog.
I don’t see why an even higher reward would not let them discover that in the end, their loyalty lies elsewhere altogether. Thus, it will be perfectly rational behaviour for companies to try to buy their agent’s loyalty back and have them shut up.
Now we have created a loyalty market, but acting on markets is what companies do all the time and should do best. When I look at the Wal-Mart bribery case, I doubt the community can keep up with the price development for long, at least when it comes to the important cases. Publicly available figures for Wal Mart de Mexico speak for themselves:
| Bribes paid in Mexico: | US $ | 24.000.000 |
| Potential damage if fined under FCPA: | US $ | 6.500.000.000 |
| Profit in Q2/2012 | US $ | 650.000.000 |
| Profits made since paying bribes in 2005: | US $ | 12.000.000.000 |
Sources: 1, 2, 3
The interesting players in the corruption game obviously have a lot to gain, much more to lose, and a vault filled with spare cash. I doubt that the reward programme was a smart move in the long run – both ethically and economically, but we’ll see.
[update 5. September 2012, 19.30 h]:
Wall Street Journal reports on a study on retaliation against whistleblowers:
More than one in five employees who reported misconduct they observed to their employers perceived retaliation for doing so, according to a new study.
The study found 22% of American workers who reported misconduct to their employers in 2011 said they experienced retaliation, up from 15% in 2009.
C. M. Matthews (5.9.2012): Whistleblower Retaliation on the Rise, Study Finds. WSJ Corruption Currents.
With the (growing) stick well established, I’m excited about who is going to be the first carrot-company.
[update 2, 18 September 2012, 9.30 h]
Bradley Birkenfeld, an ex-UBS-banker, saw the 50.000 and raised to US $ 104 million:
The Dark Side of the Moon
In September 2005, a senior Wal-Mart lawyer received an alarming e-mail from a former executive at the company’s largest foreign subsidiary, Wal-Mart de Mexico. In the e-mail and follow-up conversations, the former executive described how Wal-Mart de Mexico had orchestrated a campaign of bribery to win market dominance. In its rush to build stores, he said, the company had paid bribes to obtain permits in virtually every corner of the country.
[…]
In the interviews, Mr. Cicero recounted how he had helped organize years of payoffs. He described personally dispatching two trusted outside lawyers to deliver envelopes of cash to government officials. They targeted mayors and city council members, obscure urban planners, low-level bureaucrats who issued permits — anyone with the power to thwart Wal-Mart’s growth. The bribes, he said, bought zoning approvals, reductions in environmental impact fees and the allegiance of neighborhood leaders.
He called it working “the dark side of the moon.”
David Barstow (21.4.2012): Vast Mexico Bribery Case Hushed Up by Wal-Mart After Top-Level Struggle. The New York Times.
Germany Fails GRECO Deadline
Since it is still legal (or rather: not illegal) to bribe a German member of parliament as long as you are not buying her vote (§ 108e, StGB), Germany can’t even ratify the convention, which has been subject of much deliberation.
To monitor member states’ stance on corruption issues, the Council of Europe has formed the Group of States against Corruption (GRECO). It has the
objective […] to improve the capacity of its members to fight corruption by monitoring their compliance with Council of Europe anti-corruption standards through a dynamic process of mutual evaluation and peer pressure.
The council of Europe: What is GRECO? (ret. 3.9.2012)
In 2011 GRECO has concluded in its third evaluationthat Germany has implemented or satisfactorily dealt with only four of the twenty recommendations contained in the Third Round Evaluation Report. With respect to Theme I – Incriminations, recommendation ii has been implemented satisfactorily and recommendations i and iii to x have not been implemented. With respect to Theme II – Transparency of Party Funding, recommendation i and vi have been implemented satisfactorily and recommendation ix has been dealt with in a satisfactory manner. Recommendations ii, iii, iv, v, viii and x have been partly implemented and recommendation vii has not been implemented.
GRECO (9.12.2011): Third Evaluation Round. Compliance Report on Germany p. 15, section 72 (Emphasis original. German and French versions here – look in column »Compliance Reports«, sub-column »Version«).In the same report GRECO had also set a deadline:
In view of the above, GRECO therefore concludes that as regards the implementation of the recommendations addressed to Germany in this Evaluation Round the current very low level of compliance with the recommendations is “globally unsatisfactory” […]. GRECO therefore […] asks the Head of the German delegation to provide a report on progress in implementing the outstanding recommendations by 30 June 2012 at the latest […].
GRECO (9.12.2011): Third Evaluation Round. Compliance Report on Germany p. 16, section 75.And what do you know, the Head of the German Delegation did not answer by 30 June and he did not answer until this day. The Pirate Party has issued a press release on the issue, but that’s about it – no media coverage, no public outcry, no nothing. Germany’s dealing with the whole corruption issue continues to be a major travesty.
Cloud a la ownCloud
Sync Contacts
- Thunderbird: Sogo Connector + »more functions for address book« (optional)
- Android: CardDAV
Sync Calendar
- Thunderbird: Sogo Connector + Lightning
- Android: CalDAV
Desktop Client
- Setting it up:
Somehow it only worked as root, chown did the trick (see here):
sudo chown -Rc USER:USER /home/USER/.local/share/data - Syncing
Syncing works pretty well – but unfortunately not well enough. I do like that one can connect random folders to sync (for example a local folder »Documents« may be called »docs« on OC). What I like not so much is that you can only run two-way-sync. There is no option »sync only from server to machine« or »sync only from machine to server«. It would be very helpful as I use Unison to sync very large parts of my hard drives among several machines – much more then I want or need in OC. Yesterday I lost some data and I think it was due to owncloud got confused with two machines syncing to it in addition to syncing directly in between each other. - Android
The oc-app allows syncing to the phone on a file-by-file basis, which is neat. It also adds an owncloud-option to the share-menu. What I find really convenient though is that owncloud allows es-file-explorer to connect.
Sharing Files
Further tutorials and resources I used
- Meinnoteblog
- Points of Interest
- SoGo
- Owncloud on Webdav and this support page (very slow at the moment)
- Jamie Flarity: Make Webdav persist in Nautilus
- Techdirt has a review of various solutions, including a selfhosted gmail style email – owncloud is missing though.
[article started in August 2012; final, rewritten version from January 2014]
.htaccess redirect with GET variable
RewriteEngine on
RewriteBase /
Then, for the actual rule there’s a lot of generally helpful stuff out there – only it didn’t help me:
- the string in question was a GET-variable as part of a dynamic URL
- the string could be in the middle of the URL or at the end
My task was to replace a chunk from a dynamic URL and leave unchanged whatever was before or after this chunk.
The example was the page you’re reading at the moment. It used to be called »Recettes« and I wanted to rename it to »Recipes«.
The overview was reached through http://www.brasserie-seul.com/?Recettes, but this article had the URL http://www.brasserie-seul.com/?Recettes&nr=60. In addition this page has groups, so there is also http://www.brasserie-seul.com/?Recettes&group=web, […]group=ubuntu etc.
It took me literally hours of research, until I finally found Carolyn Shelby’s very helpful article. Her code took me almost there:
RewriteCond %{QUERY_STRING} ^(.*)Recettes(.*)$
RewriteRule ^$ Recipes? [R=301,L]
Redecorating the Place
So after six years of tiny letters and narrow columns, I made a new skin. This is how the Brasserie looked until today:
After quiet times on this website I have felt the motivation to use it more again for a while now, especially because I never was too happy with the social networking sites big and small. I made an earlier attempt when I felt the Google already knew enough and more intolerableA FB-Stories hit the news , outweighing the major advantage: low maintenance effort with high connectivity. I finally decided to get rid of both it and some major dust at the trusty old Brasserie when I read Scott Hanselman’s »Your Words Are Wasted«:
You are pouring your words into increasingly closed and often walled gardens. You are giving control – and sometimes ownership – of your content to social media companies that will SURELY fail.
After considerable restructuring and restyling work, I hope the motivation sticks for a while!
New Xampp Security Concept
New XAMPP security concept:
Access to the requested object is only available from the local network.
This setting can be configured in the file “httpd-xampp.conf”.
If you think this is a server error, please contact the webmaster.
Error 403
It is always very helpful to a) tell people to contact somone they don’t have and b) tell them to edit a file without telling them where it is and what to edit. After some poking around and several strange black magic suggestions, I found a few sources pointing towards what also worked for me. cpighin summed it up the nicest:
Open httpd-xampp.conf in a text editor – for instance by typing
sudo gedit /opt/lampp/etc/extra/httpd-xampp.conf
Then go and find the section »since XAMPP 1.4.3«. There it should say
<Directory “/opt/lampp/phpmyadmin”>
AllowOverride AuthConfig Limit
Order allow,deny
Allow from all
</Directory>
Replace it with
<Directory “/opt/lampp/phpmyadmin”>
AllowOverride AuthConfig Limit
Require all granted
</Directory>
Then restart xampp through
sudo /opt/lampp/lampp restart
Bulgaria’s Deadly Game
No fewer than twenty football bosses have been murdered in Bulgaria in the last decade. In Assignment, Margot Dunne explores reports of deep rooted corruption and matchfixing in the country’s top league.
The Right Password Manager
For instance he did show an epic laxness concerning his personal data by not obeying Schofield’s 2nd law of computing. It states »data doesn’t really exist unless you have at least two copies of it.« I do obey this law by using backintime and I recommend you use something similar.
The guy also daisy-chained password-resets and email-accounts, offering a single point of entry to his digital everything. This got me thinking about my own passwords. They are generally very strong and I have a lot of different passwords. Sometimes too many different ones, so I keep forgetting which ones I used where. But sometimes not enough different ones, as some applications share some passwords. This needs to change, so it is time for a password manager.
[update 30.8.2012] I installed KeePassX a while ago and am quite happy. I thought I had found the perfect combination when Nic mentioned the open source self hosted oneCloud, but I failed. Looking for another solution, I went for ubuntu one.
Ubuntu one does not support android 1.6 any more, but ES File manager does. And it also does support ubuntu one.
[update 26.9.2019] Bill of Pixel Privacy sent me an article on passwords which has a lot of interesting facts and figures. So if you think all this doesn’t concern you, you might want to check it out: https://pixelprivacy.com/resources/reusing-passwords/
[/update]
What are the options?
- Passwordmaker
- KeepassX
for *nix-based systems
+ independent from KeePass but they share a db-format, so you can port stuff
+ GNU & Open Source - KeePass
? Any connection to KeepassX?
+ Has a portable version
+ independent from KeePassX, but uses same db-format, so you can port your stuff
– needs wine or windows - WebKeePass
Java-port of KeePass - Revelation
- Mitto
+ apparently self-hosted - Pasaffe
+ DB is Passwordsafe 3.0 compatible - Passwordgorilla
- Passwordsafe
+ DB compatible with pasaffe
At askubuntu the majority recommends KeePassX. On stackexchange WebApps there is a thread on self hosted variants.
What are my requirements?
* sufficient cryptographic algorithm – SHA1 or MD5 won’t do.
* accessible from on the road
* Open Source
[update 21.8.2012]
I am trying KeePassX at the moment. I like the interface and have already forgotten most passwords – so what I don’t like is I started relying heavily on a piece of software. Anyway, there are at least two Android clients that can read KeePassX’ data base:
- KeePassDroid
+ requires Android 1.5 und up
+ syncs to drop box
+ good reviews
+ free
+ large user base - Walletx Password Manager
+ syncs to dropbox
– requires Android 2.2 and up
– not so good reviews
– small user base
xubuntu 12.04
1. Installation from LiveUSB
First surprise:No issues. Only: apparently all of a sudden my computer needs a /boot partition, so my partition map looks like this:
1. primary ext2 254MB /boot
2. logical swap 4000MB
3. logical ext4 <rest> /
2. Dual Screen under xubuntu
sudo apt-get install arandr
The Shocking Truth
In her article she sheds much light on the many (dim to dark) issues related to the Occupy-movement, and explains how the Department of Homeland Security, local mayors, congress, Wall Street, and businesses are linked to each other and ultimately to OWS.
Feeds a la Tiny Tiny RSS
[update 2011-11-10] Both this and Nic’s article have been featured on tt-rss’ project site. There are a bunch of other interesting and useful articles, too, so check it if you’re interested in tt-rss. [/update]
A while ago, Google updated their reader, killing one of the best features: sharing. I looked around a bit for a suitable alternative and in the end settled with tiny, tiny rss.
Advantages:
- It runs on my server, so nothing can be done to it unless I approve
- Sharing is easy
- It’s simple
Nic, who thankfully came up with this great alternative, has a more techno-philosophical article on the switch.
Some minor issues I had while installing:
1. open_basedir not supported
Problem: during installation I got the fatal error
php.ini: open_basedir is not supported
Solution: Open <tt-rss-root>/sanity_check.php and find the entry Update: in recent versions it’s in <root/include>
if (ini_get(“open_basedir”)) { $err_msg = “php.ini: open_basedir is not supported.”; }
Convert LaTeX to .odt
Shooting of activist »unfortunate«
Cross-Distro Live-USB
Here is your way out: UNetbootin
- Download
- sudo chmod +x <downloaded file>
- Optional: install p7zip and p7zip-plugins
- ./<downloaded file>
- Happy
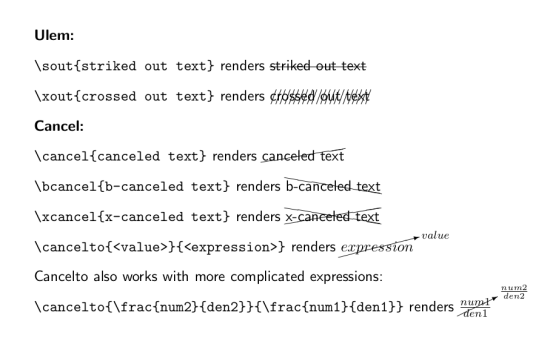
Strikethrough in LaTeX
Strikethough in LaTeX using »ulem«
\usepackage{ulem} in the preamble gives you two ways to strike out text (and a couple more for underlining):
\sout{text to be striked out}for a horizontal line through text to be striked out (exactly like »line through«).\xout{text to be crossed out}for many short diagonal lines crossing out the letters of the text to be crossed out
The problem that ulem affects some bibliography styles where otherwise italicised text is then underlined can be remedied through the »normalem«-option in the preamble: \usepackage[normalem]{ulem} (Thanks Fredrik!).
Ulem is part of MiKTeX and TeX Live but also available at ctan.
Strikethrough in LaTeX using »cancel«
\usepackage{cancel} in the preamble gives you four different modes of striking through
\cancel{text to cancel}draws a diagonal line (slash) through its argument\bcancel{text to cancel}uses the negative slope (a backslash)\xcancel{text to cancel}draws an X (actually \cancel plus \bcancel)\cancelto{〈value〉}{〈expression〉}draws a diagonal arrow through the 〈expression〉pointing to the 〈value〉 (math-mode only)
You can get cancel at ctan.
Results
Click on the image for pdf or download the source file – which looks like this:
\documentclass[a4paper,11pt]{article}
\usepackage[utf8]{inputenc}
\usepackage{setspace}
\usepackage{ulem}
\usepackage{cancel}
\begin{document}
\sffamily
\doublespace
\textbf{Ulem:}
\verb+\sout{striked out text}+ renders \sout{striked out text}
\verb+\xout{crossed out text}+ renders \xout{crossed out text}
\textbf{Cancel:}
\verb+\cancel{canceled text}+ renders \cancel{canceled text}
\verb+\bcancel{b-canceled text}+ renders \bcancel{b-canceled text}
\verb+\xcancel{x-canceled text}+ renders \xcancel{x-canceled text}
\verb+\cancelto{<value>}{<expression>}+ renders $\cancelto{value}{expression} $
Cancelto also works with more complicated expressions:
\verb+\cancelto{\frac{num2}{den2}}{\frac{num1}{den1}}+ renders $\cancelto{\frac{num2}{den2}}{\frac{num1}{den1}} $
\end{document}
Deny Internet in Ubuntu
- Connect to internet using a modem
- Connect to wireless and ethernet networks
- Use modems
I thought that should do the trick, yet it didn’t restrict internet access to this user. I tried various other things to deny access to network and web and finally found something useful at ubuntuusers.org (German):
create a file in /etc/init.d (filename doesn’t matter)
sudo touch /etc/init.d/iptab-filter.sh
Open the file you created:
sudo gedit /etc/init.d/iptab-filter.sh
ffmpeg-GUI
I was unable to convert to this with avidemux. Google quickly told me that ffmpeg could do the trick. But being unfamiliar with bitrates and stuff I was happy indeed when I found Mobile Media Converter, which is a neat and lean GUI for ffmpeg (Mac, Linux and Win). It even sports convenient batch process via drag & drop. Have fun.
Fonts in LaTeX
\usepackage{palatino}
\usepackage{times}
\usepackage{bookman}
\usepackage{newcent}
or, for standard post script fonts
\usepackage{pslatex} or
\usepackage{ae,aecompl}
Position:Absolute in LaTeX
In the preamble
\usepackage{textpos}
In the document
\begin{textblock}{2}[0,0](8,1.5)
Lorem ipsum dolor sit amet
\end{textblock}
The arguments are as follows:
\begin{textpos}
{<width>}
[<left handle>,<top handle>]
(<leftmargin>,<topmargin>)
World Wide Food Chain
As soon as the smart guys make the security hole public, the swarm of pimple stricken milksops with teenage angst who read what the smart guys publish come marauding. They upload a bit of this, toy around a bit in that and then claim they »hacked« something while they really only hacked their pants once more.
This way the smart guys don’t have to bother telling the people about their security holes (probably assuming backup copies and a restore script anyway; if this doesn’t exist – more valuable lessons learned): they have their monkey baggage to do so for them.
Section Footnote in LaTeX
I wanted to have footnotes from inside sections, subsections, and subsubsections. They work similar to footnotes in tables, you need to address them similar to this:
\section{Some Section in my Document\footnotemark}
\footnotetext{My boring footnotetext.}
Only, when I did it like this, it worked on some occasions, but not on others (reason for me biting the wood).
I finally found out that it did not work on all occasions where I did it exactly like in above example, but always rendered
TeX capacity exceeded, sorry [input stack size=5000]
However, it did work on all the occasions where I specified the (optional) short title for section/subsection/&c:
\section[Section in Document]{Some Section in my Document\footnotemark}
\footnotetext{My boring footnotetext.}
The optional shorter title appears — as far as I know — in the table of contents and in left-/rightmark. Also, Kile uses it to display the document structure, too. So if you have rather long titles (like I do) it is a good idea specifying a short one anyway. If not, I guess you can just as well repeat the full title in the optional argument if you need a footnote.
When using the starred variant (\section*{My merry section}), don’t provide a short title.
Continuous Footnote Numbering in LaTeX
Create a folder <remreset> in your local package repository. Save the file remreset.sty into this folder.
Open your preamble and add
\usepackage{remreset}
\@removefromreset{footnote}{chapter}
Should you get an error message like this
You can’t use ‘\spacefactor’ in vertical mode. \@
or like this
Command \@ already defined.
embrace the stuff with \makeatletter and \makeatother:
\usepackage{remreset}
\makeatletter
\@removefromreset{footnote}{chapter}
\makeatother
Voilà.
ΛαΤεΧ in Greek
$\Gamma\rho\varepsilon\varepsilon\kappa$gets you Γρεεκ allright, but it looks clumsy and lacks all the accents etc.- betababel. It does not work with my customised control sequences, and I am too lazy to change them and learn them all anew.
- polutonikogreek. Neat, slim, worked straight away.
Nos. 2 & 3 use ngerman, so make sure they don’t start a fight with german.
update
I had a slight problem with polutonikogreek and titletoc. Whenever I used something like
\greek{p’olemos}
which referred to this entry in the preamble:
\newcommand*{\greek}[1]%
{\selectlanguage{polutonikogreek}{#1}%
\selectlanguage{german}}
the .toc-file looked like this at the corresponding place:
[…]
\contentsline {section}{\numberline {1.1}KAPITEL-1.1}{14}
\contentsline {subsection}{\numberline {1.1.1}UNTERKAPITEL-1.1.1}{14}
\select@language {polutonikogreek}
\select@language {german}
\select@language {polutonikogreek}
\select@language {german}
\contentsline {subsection}{\numberline {1.1.2}UNTERKAPITEL-1.1.2}{20} […]
Wherever \select@language appeared in the toc, the styling of my toc entries of the subsection level was being messed up. I style subsection entries in the toc in a way that they all get written in a single line. It looks like this:
\titlecontents*{subsection}[3.5em]
{\vspace{-0.5mm}\itshape\footnotesize}{}%
{}{\dots\normalfont\footnotesize%
\thecontentspage.\enspace}%
[\itshape][\vspace{1mm}]
There are two solutions.
- Ignore the problem, compile your document, open the .toc-file, delete all
\select@languageentries and compile again (but only once). - Use the following specifications in your preamble:
\usepackage{ucs} \usepackage[utf8x]{inputenc} \usepackage[polutonikogreek,german]{babel} \newcommand{\gdir}% {\foreignlanguage{polutonikogreek}}and then put the greek text directly into your document like this:
\gdir{Πόλεμος}
Custom Counter in LaTeX
How it does work:
Here is what we do: We define the counter
\newcounter{MyCounter}
then we add
\renewcommand\theMyCounter{\roman{MyCounter}}
after it, and it works. Thanks to Axel for his help on this.
How it does not work:
When you define a new counter like this
\newcounter{MyCounter}
And later use it like this
\refstepcounter{MyCounter}\label{example}
\roman{MyCounter}. Beispiel eins
And then reference it like this:
And now I reference an example \ref{example}. \end{document}
Then LaTeX still interprets it as something like
\newcommand\theMyCounter{\arabic{MyCounter}}
So it results in an arabic number. This is not what we want. We want to reference the counter in lower roman (or upper roman or alph or what have you), too.
Timestamp your LaTeX Documents
\usepackage{timestamp}
in the preambel and
\timestamp
anywhere in your document, you can then add the – you’re guessing it – timestamp. The output will look like this:
2007-03-23 14:34
Now, I never liked this date format, so if you, too, prefer DD-MM-YYYY, open timestamp.sty and scroll to the very bottom. Replace
\newcommand{\timestamp}{\the\year-%
\ifnum\month<10 0\fi\the\month-%
\ifnum\day<10 0\fi\the\day\ \xxivtime}
(the last three lines above \endinput) with
\newcommand{\timestamp}{\ifnum\day<10 0\fi\the\day.\,%
\ifnum\month<10 0\fi\the\month.\,%
\the\year\ — \xxivtime\,h}
\timestamp then produces
23. 03. 2007 – 14:34 h
However, the version I use looks like this:
\newcommand{\timestamp}{compiled on \ifnum\day<10 0\fi\the\day.\,%
\ifnum\month<10 0\fi\the\month.\,%
\the\year\ at \xxivtime\,h}
So the output reads
compiled on 23. 03. 2007 at 14:34 h